Steve Riley: The benefits of SSE or security service edge is and a SASE journey, is very clear. It is the first time to me, it's that perfect reset for security. They get to move the majority of their inspection points closer to the user, closer to the data. They get to move it out of the data center to the cloud, right? Where it can be applied everywhere data goes everywhere user.
Producer: Hello, and welcome to Security Visionaries posted by Jason Clark CSO at Netskope. Right now we are smack in the middle of one of the biggest evolutions in cybersecurity, both in the last 10 years and in the decade to come. This is the feeling driving today's very special episode on the release of the first ever Gartner Magic Quadrant for Security Service Edge, which establishes the framework for how security will need to be delivered in the cloud and the company's best equipped to provide it including Netskope. In this episode, we bring you a conversation with Steve Riley, a former Gartner analyst and current field CTO at Netskope who has played a major role in many previous Magic Quadrants. Steve sits down with Jason to discuss the recent Magic Quadrant for SSE provides details on the whys, the whats and the hows of SSE and underscores why this is so important to the future of security. This is Security Visionaries. Before we dive into Steve's interview, here's a brief word from our sponsor.
Ad: The Security Visionaries podcast is powered by the team at Netskope. Netskope is the SASE leader, offering everything you need to provide a fast data centric and cloud smart user experience at the speed of business today. Learn
[email protected] Producer: Without further ado, please enjoy the special episode of Security Visionaries with Steve Riley, field CTO at Netskope and your host. Jason Clark.
Jason Clark: Welcome to security visionaries. I'm your host, Jason Clark, CMO and chief strategy officer and chief security officer at Netskope. And today I am joined by a very special guest. Steve Riley, Steve, how are you?
Steve Riley: Very good, Jason. Thanks. How about yourself?
Jason Clark: I am super fantastic. Today is a fun day because there's some big news that just hit that we're going to talk about. And so that'd be little fill a lot of our conversation that the listeners will enjoy, but let's maybe start with just you introducing yourself and describing, cause you're most famous for being a Gartner analyst, right? And the creator of the first Magic Quadrant for CASB, which was been a pretty big deal. So maybe you can describe, talk through that life and of being a Gartner analyst and the creation of the Magic Quadrant and just a background about yourself.
Steve Riley: When I was a Gartner, I covered pretty much everything to do with public cloud security. So I would get questions from folks about how to be secure in IAS environments, AWS, Azure, a little bit of GCP, SASE environments, mostly office 365 smattering, a few others. And then of course when the CASB MQ work started, I began taking a lot of inquiry about that too. So a typical day for me would be five hours of conversations with clients. And then the remainder of my day, I would be dividing between things like writing, research, reading, other things, to formulate new ideas, conducting some analysis of the stuff that I had collected. And then peer review is a big component of that. No Gartner research goes out without another set of well, multiple sets of eyes taking a look at it to make sure the opinions are sound and that there's some consistency in it.
Jason Clark: So, what were your coverage areas?
Steve Riley: So anything about public cloud security, lots of stuff about AWS and Azure security. I didn't get too many people asking about GCP security. I just don't know if Gartner clients use Google cloud very much. I had a lot of office 365 security inquiry. In fact, the first note I wrote was about how to be secure in office 365. And then of course the CASB and the ZTA inquiry began to ramp up after I wrote the first documents on those two markets.
Jason Clark: I feel like the GCP aspect, I think that's changing fast. I see a lot of discussions around GCP, in a pretty big way, I'd say over the last 12 months, faster than I've ever seen. So I'd say it's probably starting to hit heavy, but how did you avoid boredom, you once told me that your wife said she could do your job because you just say the same thing over and over and over and over again, right, and I thought, okay, like how do you manage boredom then?
Steve Riley: Well, it's true. Many of my conversations would sound the same if you only heard my half of it, which is what she would hear, right. My half. And it doesn't matter what the other person says. I'll just say the first thing, pause, I'll say the next thing, pause, say the next thing like, well, it's not quite like that. What made it interesting was hearing the other person, hearing the client, what did they want to learn? What were they trying to solve? What thorny issues were keeping them from advancing? So it's true that most people face essentially similar problems, but there was always a different set of context or something unique about it that allowed me to sit in front of my computer for five, sometimes six hours a day and have what might have sounded like the same conversation, but always learn something new from it. So that's how I avoided getting bored was I usually learn something.
Jason Clark: So what percent of customers that you would talk to? Wow [inaudible 00:05:42]
Steve Riley: Not a whole lot. I can remember some instances of where I could tell that I was speaking with a client who had already been thinking a lot about cloud security and they were trying to optimize what they were doing. Most of my conversations though, were with folks who were just getting started in the cloud. So, how do I transition my thinking away from on-premises appliance based to this idea of subscribing to stuff where the security controls are coming from the people who are also providing me the rest of the infrastructure. So I don't want to say that smart people don't need Gartner and that it's only stupid people who use Gartner. That's not absolutely true at all, but from the perspective of my coverage area, since it was solely dedicated to cloud security, which was still new for quite a lot of folks, most of my interactions tended to be at that sort of beginner to an intermediate level. And I was totally okay with that. I didn't mind that at all.
Jason Clark: I was in London watching you on stage. There's something you said that stuck with me since then. And it was the big difference in security is that data is no longer on a CPU that you own or control. And I was like, wow, that's the simplest one sentence way to say it, that changes everything. And as you think about that, and that's where CASB and why your love for cloud security, right? As you have drive this change, how long did you predict that the CASB MQ would stick around before the market demanded convergence or a change?
Steve Riley: Well, the first iteration of the MQ was in the end of 2017 on Halloween, at the 2018 security risk management summit. I was doing a theater presentation on the Magic Quadrant. So these are just like 15 minutes of where you talk through what the market is and why the vendors landed, where they did and where you think it might go. Somebody asked me that question, how long do you think this market's going to last? And I said, I figure, we'll probably do three more iterations of this MQ before the market [more 00:07:52] sent us something else and we'll need to write another MQ. And my manager's manager was standing in the back with his arms folded, shaking his head, no, no, no. Because MQs are revenue generating things for Gartner, but it turned out to be right.
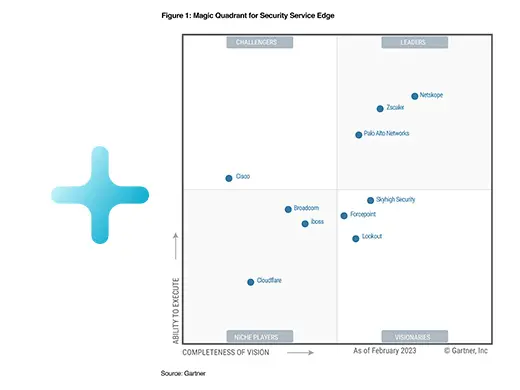
Jason Clark: So, okay. So let's just get straight to the big news. So today the Gartner announced a new MQ, which is called Security Service Edge, which is part of the SASE kind of framework or journey, right? And what it does is collapses and says, look, there's no more secure app gateway MQ, right? There's no more CASB. And it takes in everything's ZTNA, along with a number of other aspects and so, this is now one platform, one MQ. I see this as something that is probably the number one biggest thing that happened the cybersecurity in the last 10 years, and definitely for the next 10, this is really big, biggest transformation I think I've ever seen. And you were a major part of that. Can you talk a little bit about SSE, your involvement in the creation of this thing and the proponent for it, and also why is a new MQ and why are the other ones going away?
Steve Riley: My co-author with the CASB Magic Quadrant and critical capabilities. Remember, these are always most useful when you look at the pair of them, we're in the middle of 2020, we started thinking, hey, you look at the vendors in the CASB MQ, and then the SWG MQ, there's a lot of overlap and we also saw that the vendors themselves were starting to overlap. So we proposed to the rest of the analyst community that we need to have the research reflect what's going on in the market. And more importantly, what people were wanting to buy, folks were looking to consolidate, vendor consolidation is real. And so we need our research obviously to reflect what's happening in the market and where we think the market is going to go. Now, initially, when we made this proposal, not everybody agreed. There were some other folks who were comfortable with what they were doing. They didn't think that CASB was going to be that big of a deal that on premises security is still going to be huge. But the reality is, if you look at the forecast notes that Gartner publishes, while it's true, that the dollar value spent on cloud security over the next several years, won't be as much still as the on-premises. The growth is much higher. So, on-premises is going to idle while cloud security spent and just goes to the roof. So we needed to create this new Magic Quadrant that represented the consolidation. And there was initially some thinking that, well, we'll just retire the CASB MQ and push the SWG MQ to be both. And Craig and I didn't like that. We wanted to send the right message, which is both of these markets as standalone entities have reached the end of their lives. And you do that by retiring both MQs, you create a new MQ that has a new name, and tell where the history is. But what's really interesting that I didn't expect, this decision was made after I left Gartner in March of last year, that the SSE MQ would also include ZTNA, I think that's absolutely the right thing to do. So there won't be any more ZTNA market guides probably, but it totally makes sense to have one mechanism, one platform that has visibility into and control over all of your data, no matter what lane it happens to be in.
Jason Clark: So I kind of think about it, like there's a user going to an app, and we've always added new tech depending what type of app the user's going to, or where the app or where the user was. And we were constantly trying to solve that from on-prem and stretching security, which created friction on the business, on the security team, et cetera. But I guess in the simplest terms, let's say, a lot of people have a cloud proxy to protect cloud traffic, a web proxy to protect web traffic, and then a zero trust slash VPN solution for private apps, right? Access of a user that's remote, going to an app at the data center. That's three different technologies. When the reality is you're trying to solve the same problem. It's stop threats is protect data, it's manage access, right? I mean, that's just kind of crazy when you think about why did we ever do that? It does just make sense, Steve, the vendor consolidation and it is the same problem. You should have one single inspection point for anything use at app, but what was the moment that helped drive the thinking? Because obviously you had people saying, no, it is just all move to SWG versus it should also all move to CASB, right? So your cloud proxy and web proxy, what was the major data point or a thing that happened, that convinced everybody that cloud was actually a little bit more important or a lot more important and it should be a new MQ?
Steve Riley: I would say it was finally the realization that most of an organization's critical traffic has moved outside of the data center. So from one data center to many centers of data. And if you think about, especially with SaaS, that could be hundreds or thousands of centers of data, and most SaaS applications have very little to note built in security controls. Perfect. This is what made CASB so critical in the early days and still critical today. I almost hate to say this, but I'm going to anyway. It's actually maybe the first instance we've ever seen where built on security works. If you have all your SaaS traffic flow through the CASB, then you get all this great inspection, DLP, the threat neutralization, maybe you were used to with just your SWG. But the only thing your SWG knew about was talking to the internet. We can do this great stuff with one product CASB for every single SaaS application that somebody might be subscribing to. Well, then it's only natural to think, why would I need one product for internet, one product for SaaS and one product for internal apps when they're all doing the same thing, I want DLP across all those. I want threat neutralization across all of those. I want some ability to provide granular control over activities, maybe based on whether they have a managed or an unmanaged device. And can you imagine how complicated it would get if you've got duplicate device policies and duplicate DLP policies and duplicate access policies across three different categories with three different consoles and people arguing over who gets to sit at which console, it became an almost impossible position, which is why a lot of clients responded, yes, when Gartner did a survey a couple years ago, asking where are you in your security vendor consolidation path, over 70% of the respondents either had started that, or they were planning to start it. Even if they thought it would cost a little bit more in the short run, because they were anticipating significant cost savings in the long run with reduced administration overhead, that sort of thing.
Jason Clark: Yeah. The benefits of SSE or Security Service Edge and a SaaS journey. It's very clear, right? Like it is the first time, to me, it's that perfect reset for security. They get to move the majority of their inspection points closer to the user, closer to the data. They get to move it out of the data center to the cloud, right? Where it can be applied everywhere data goes everywhere user goes. I mean, it changes the game and the way that they can enable the business, for M and A or stop saying no to things, right? I hate the word when people talk about shadow IT, I think about no that's business IT, it's our job to manage that and help them do it safely. Right, you can't do it sitting in the data center because most of it's SaaS now, right? Most companies have a thousand SaaS apps and then you consolidate, so you get the cost benefit function, but then your team to start managing things as one solution in the cloud, not having to do all sorts of patches, which everybody was pretty much doing all of December with the new vulnerabilities out. Right? So you start removing all the operational complexity. It's just nothing but goodness, in every way, better user experience, better happier security in network teams, happier executives. It's just the business outcomes, add up, add up, add up.
Steve Riley: People have for years think about the theory of policy. They talk about things like policy decision points and policy enforcement points. You could go back to some of the old Jericho form stuff from 20 years ago. If you can still find it online anywhere and read through some of these ideas, SSE actually makes it real, you centralize policy decision and you centralize policy definition too. So you could say, overloading the D part, but you're distributing the policy enforcement as close as possible to wherever the data is being accessed. So it surrounds the data, it surrounds the workers and it's something that people have been wanting to get out of their security products for years. But with SSE we can finally get it, right? The business value comes from a single platform that eliminates the redundancy. We talked about a few seconds ago, a single policy enforcement model that simplifies reporting and compliance. And that's really important because all cloud using organizations, in other words, all orgs are going to have to demonstrate that they've got the cloud under control. So here's how you do it. SSE gives you a single pass for all lanes of traffic for all types of traffic. So that helps maintain performance users basically won't notice it if the SSE is implemented, right? Yet a single agent, which simplifies day-to-day management and a single console. Now, what's really important here though is, some organizations may still want to delegate different functions to different teams. So it's good that you can do that in the console.
Jason Clark: Yeah. I have definitely been part where I've seen teams let's call it the VPN team say, no, I want my own VPN solution where the other teams cannot manage my console, right? And it's like, and so you do sometimes have where people want to drive their own views, their own control, or even their own product, which is not efficient and effective for their organization, but certainly the delegation of rights, right? And what they manage is, and that's why I think ... So a lot of these, as we talk about consolidation, these decisions need to move higher up in the organizations, to the CISO and to the CIO so that people are not making it biased based off of that one particular organization's needs, but overall, right? The entire as a whole. So as we think about something kind of like we talked about SSE versus, invoice SASE. So SASE was what came pretty big topic, very fast. What is the difference of Security Service Edge or SSE versus secure access Service Edge.
Steve Riley: Service edge? Well, SASE, even in the early days, there were arguments again over, is it an architecture? Is it a product? Is it a journey? I think most people have become comfortable with the notion that SASE is an architecture and it represents a journey, but it's an effort to illustrate the consolidation underway between networking and security, formerly separate groups who probably tried to do everything they could to avoid interacting with each other, both professionally and socially, just wasn't working anymore and forward thinking orgs were already blending the functions together. And so it made sense to start thinking about an architecture where they were brought together. Now in the early days of SASE, there was this nice diagram that had two parts. There was a left hand side and a right hand side. The left hand side was all of the networking functions, but they were going to be delivered as a service now as opposed to buying 18 different boxes, SD-WAN, WAN optimization, DNS. Several other things on the left hand side, the right hand side was security as a service. And it had CASB and SWG and ZTNA went in there. What happened though, is that SASE maybe became too big. And in fact, Gartner modified their definition of SASE, Lawrence Orange's presentation at the security and risk management summit at the end of 2021, showed a simplified version of SASE where the left hand side, remember the networking side had one item SD-WAN, all of the rest of the stuff he had removed. So we can read into that, that the only reasonable networking function to deliver as a service would be SD-WAN, some of the others, maybe we just don't need anymore. Jason Clark: So basically you're saying SASE is SSE plus SD-WAN.
Steve Riley: Yeah, you got ahead of me there.
Jason Clark: Yep, therefore, as long as you have an SSE solution, you could combine that with any SD-WAN solution, integrate them and you have it, your full SASE.
Steve Riley: Yeah. The nice thing about SSE is that, so it's the right hand side of SASE and now it's got its own MQ. So it's sort of in line with the left hand side, the networking stuff, but they don't need to be from the same vendor, SSE is independent of the underlying network. It doesn't matter. How are you going to get the bits to the SSE, you want to get all of your traffic there? Absolutely. But how are you going to get it there? SD-WAN, MPLS, Metro ethernet, IP over Avian Carrier. It doesn't really matter. SSE just doesn't care. So what's most useful is that the SSE vendor you choose has good ways to integrate with an SD-WAN partner, but they don't have to be from the same vendor. No.
Jason Clark: Okay. That it's really good. I think that's going to be very helpful for our listeners, because there is a lot of confusion there. So talking about SSE let's come back to that, because it's such a big deal, right? It's clearly a two horse race. And I think that you're looking at essentially the two cloud based organizations is Zscaler and Netskope as the leaders, then you have a third one, which is McAfee close to the bottom line, kind of their legacy technology, right? Trying to also do cloud at the same time which is very hard and being private equity right? So it's very hard, but you have those three, which I imagine most all new people going this path would probably choose something between Netskope and Zscaler. What do you think Gartner will be advising people around? Is there a calling and inquiry in which you did? I mean, how many inquiries have you done in your life?
Steve Riley: Oh, 1000 a year, times five and a half years.
Jason Clark: All right. So 5,000 inquiries that's now I know why your wife says that you just said the same thing over and over again. What would a Gartner analyst probably be saying as somebody called in, right? And said, all right, look, there's this new SSE, you've told me why to do it, but as I look at this, how do you guide me? Like do I take two of these vendors or I take three of the vendors or how are they different?
Steve Riley: There are some things that companies should think about as they look to move to SSE, don't make it an isolated project, capitalize on whatever you might already be doing for a remote worker and branch office transformation and integrate SSE into that project scope. We've seen a lot of SSE deployments succeed. When you take that attitude, as far as who you're going to look at, there's a few things I'd like to suggest, make sure that the consolidation is real. This is how you can reduce complexity while staying secure and protecting from common contemporary threats, as opposed to old fashioned threats from when everything was in the data center, make sure that all of the components of the SSE follow up common configuration and policy management and reporting model, this is the evidence that you should look for to know that what you're evaluating is truly an integrated platform. And it also eliminates the risk that disjointed components might have, like gaps or inconsistencies, speaking of inconsistencies, make sure that are no overlapping controls. So for instance, you want one DLP console for all components rather than separate DLP for SWG, for CASB proxy, for CASB API and for ZTNA, I guarantee you, disjointed, separated DLP like that is going to result in policies that don't match or inconsistent behavior. And it's going to be real head scratchy to try to figure out how to fix that. Some other things, look for a single agent. This makes it simpler to manage across your estate. And as you're looking at the console, make sure that different portions can be delegated to different teams. It may be the case that not everyone is going to be wanting to look at the same console. So you could simplify that for folks. Now make sure that the SSE evaluating operates independently, any specific kind of network architecture or infrastructure. There really shouldn't be any dependency between the two there. And the last thing I'd like to ask is that you don't overlook performance and availability. If you are sending all of your traffic to an SSE provider, they'll need a fast network with points of presence everywhere your people are, or might need to visit. Two things to look out for here. One provider who allows you to connect from anywhere to their network, without paying extra money for the privilege and to a provider who offers a performance service level. I'm reluctant to think that all of the sudden the question will be help me pick an SSE. SSE is brand new, nobody knew about this before the MQ came out, right? It's not like Gartner makes announcements on these things usually. So people aren't going to know to ask for an SSE, they're most likely, still going to be saying, hey, I need to do a better job of governing and protecting my SaaS or, I need to get remote access into private applications, or I need to do some web filtering. Maybe they'll still say web filtering. [crosstalk 00:28:14].
Jason Clark: So they're bringing a problem.
Steve Riley: They're going to bring up problem. Yep. And so what I would do in inquiry now is say, the market for those individual things has consolidated and we've created a new MQ for an SSE, have you seen it? No. Okay. So I'd bring it up and share it on the screen with the client. And I would basically talk them through what the market is and why the various vendors are where they are. Some people come to an inquiry already knowing which vendors they want. Others may not know anything at all and they're using the MQ as a way to sort of make the decision easier.
Jason Clark: Where they generally picked two or three vendors to POC.
Steve Riley: I would say the mix was right down the middle, half the time it was two and half the time it was three. I never saw anybody shortlist with four.
Jason Clark: Yeah. That makes sense.
Steve Riley: I want to say that Gartner's analysts create opinions and they become Gartner positions. So everything in Gartner analyst rights is a supported opinion. Now we try to make it based in fact, of course. So when we write the strengths and cautions, and when we put a dot in a place, those are based in facts that we assemble from various sources, not only the demo, but an RFI where we ask several questions and we can look at the answers to those questions that are influential in the MQ dot placement. We would also look at peer insights, maybe have conversations with some vendors, customers, although COVID made that more difficult. So we stopped that for the last couple years. There's a period of time where vendors can do a fact check and the idea is, did we misinterpret something and get a fact wrong? There is extra work. There's a function of Gartner called the ombudsman. And the ombudsman's job is to ensure that we analysts are following the methodology and that we're not letting our opinions become substitutes for facts.
Jason Clark: That's a weird name on ombudsman.
Steve Riley: Yeah. But newspapers have them too. Yeah. And it's kind of the same function. But anyway, so the escalation would be difficult if a vendor was really unhappy and wanted to push. So, Craig and I would have to create more evidence to show why we did a score, but the way we did and anytime we had to do that, we were successful.
Jason Clark: Yeah. But it doesn't sound like that's a fun process though. So we talked about where SSE is going to go, the evolution of that, right. So clearly we've seen that 65 to 80% of the traffic is now plowed, right? It's not people going to the NewYorktimes.com to do work, right? That ZTNA is going to apps and very much where you essentially need an upside down CASB, right? You're wanting to control the app just like you do at SASE app. And so that all makes sense, right. We've seen that go. And also that I think that a big element of SSE, like I look at SSE like a nervous system, it is, you're hearing your smell, the taste, right? Your touch, all these senses, seeing all come together to a brain. And that brain is really like a common, it's really a data protection, that's why we exist and that's the grand strategy of security, protect data. And so it brings it all together, but as you think about that and what is the future of SSE like? How are they going to continue to evolve and add components? How fast Steve will do you believe people will stop buying individual SWGs and individual CASBs and go all SSE, right? So it's a two-prong question. How fast will people be really buying SSE as a product and not individual, and what's the future?
Steve Riley: The main components, the CASB and SWG they're mature. I was moving the CASB dot very fast on the hype cycle when I owned that profile. ZTNA is still new-ish, but I think it's unlikely to emerge as a standalone market now that we're seeing so much interest in the CASB and SWG vendors to add ZTNA and it totally makes sense for what you just said, Jason, you compared ZTNA to an upside down CASB. It's really interesting to hear you say that, because that was one of the mechanisms that I would use sometimes to describe ZTNA to customers, they already know what a CASB is. If you could pick your CASB up and turn it around so that it pointed at your internal apps, instead of a SaaS app, you basically get the same functionality and light bulb that would work for folks. But no markets are static. At least no good markets are static. So I would imagine that SSE evolution would be characterized by assembling a [Creedy 00:33:19] acquiring whatever verb you want to use. All of the capabilities necessary to ensure continued and well governed, safe cloud use. So things like posture management, entitlement management, what I like to call end party risk because the SaaS application you might it be using, could in fact be just like a force.com product. So you subscribe to this force.com app, then running inside a Salesforce instance. Well, not in case of Salesforce, but in some other SaaS app, that's probably running on a private cloud, I'm sorry, a public cloud. So you can think about what does a risk chain look like? And third party, fourth party, fifth party risk, how do you ensure that no matter where you are storing your sensitive data, which could include your customers sensitive data, where are all of the potential touch points where that data could be inadvertently exposed? And I think that's one of the things that SSE is going to get really good at, is illuminating all of this end party risk so that people can make well-informed decisions about what to store their data.
Jason Clark: That's big Steve, because that is probably I'd say the number one risk that's out there that people just don't have a handle around. It is the end party risk, it's third, fourth, fifth, sixth party risk, but once you know what your users are sending data to, what devices they're taken to and the risks around any infrastructure they've put their data and then where that data's going from that infrastructure to another infrastructure, to another app and then the risks around those that it does eliminate it all, right? And that ends up being like the security Nevada of where your security controls follow the user and the data which we don't have today. So of that's huge. If we can get the SSE to be that, which if you think about it today, we kind of do these one time risk assessments. A lot of people I talk to do one time risk assessments of 365 or twice a year, versus how about in real time, you know at any moment exactly what the risk is of every single piece of data you have sitting anywhere, period. Right? And if one thing changes right? One the user or one network or one device or one app or one piece of data, anything changes, you know when that likelihood or impact just became unbearable, right? To the risk equation.
Steve Riley: I would go so far as to say that well developed SSE products under a well managed environment could give an organization more visibility and control than they ever had when everything was in the data center, because it was actually pretty easy. I can remember in some of my earlier careers, I could build a server, plug it into the land, nobody's going to know, right? And I could tell my community of people about it. And the IT department could be kind of like blind to this stuff. I really do wonder how much shadow IT was actually under desk IT as opposed to SaaS.
Jason Clark: Oh yeah, when I started as a CISO for a fortune 100, 140,000 person company, I discovered that we had 1200-
Steve Riley: There you go.
Jason Clark: Under the desk internet connection.
Steve Riley: And somebody brought in their own a little Wi-Fi that they brought it best buy. And ...
Jason Clark: I mean, it was- [crosstalk 00:37:28].
Steve Riley: [crosstalk 00:37:28] Wild, right? But-
Jason Clark: So look, Steve, this has been amazing. It has been enlightening to share your experience of kind of the ups and downs of creating an MQ of being an analyst of this new MQ of SSE, which I do again, will reiterate is probably the biggest thing that will happen in cyber security for the next 10 years. And definitely in the last 10 years, anything that even compares, it's such a smaller market. Something like, I remember when people thought EDR and AV were different markets, and now it's XDR and that convergence, this is 10 times bigger because it's the entire network perimeter moving to the cloud, right? So it's such a big moment. And thank you for being here on the day that this MQ gets released and having this is discussion and helping all of our listeners.
Steve Riley: You're very welcome. I thank you for the opportunity to have this interaction.
Ad: The security visionaries podcast is powered by the team at Netskope, looking for the right cloud security platform to enable your digital transformation journey. The Netskope security cloud helps you safely and quickly connect users directly to the internet from any device to any application, learn
[email protected] Producer: Thank you for listening to Security Visionaries, please take a moment to write and review the show and share it with someone you know who might enjoy, stay tuned for episodes releasing every other week. And we'll see you in the next one.